
- December 27, 2022
- C. Imran
- 0 Comments
- Cyber Security
Risk & Vulnerability Assessment
What is Vulnerability Assessment?
Vulnerability assessment is the process of identifying, classifying, and prioritizing security vulnerabilities in a system or network. It involves scanning systems and networks to detect any weaknesses or weaknesses in security protocols that can be exploited by malicious attackers. It is also used to identify and prioritize areas where security should be improved. One way to do this is by using tools like a active and passive scanning. This will tell you what areas may need improvement and help you identify any potential risks.
5 Must-Do Steps for a Thorough Vulnerability Assessment
Using the right tools to scan your systems and networks is an important first step towards knowing what vulnerabilities your systems have. But what’s even more crucial is understanding how to interpret those vulnerabilities, or you could end up making things worse instead of better, leaving yourself vulnerable to cybercriminals rather than safeguarding yourself against them. Here are few must-do steps for a thorough vulnerability assessment.
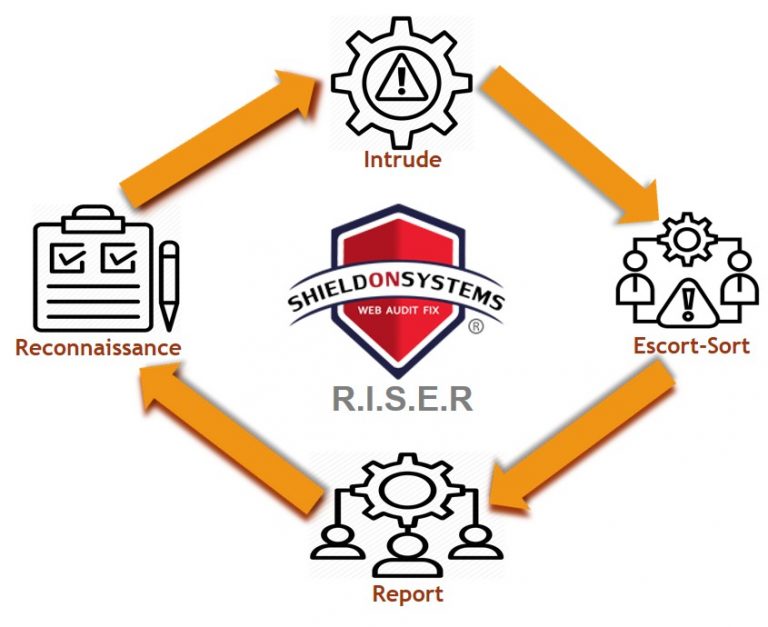
SOSWebAuditFix R.I.S.E.R Methodology
A web safety evaluation is not an easy process. It takes time, research and investment. There are many nuances in assessing the risks of vulnerabilities and different strategies to mitigate them. Ultimately, the organization must develop an appropriate risk assessment strategy and implement security controls that will protect their data while complying with industry regulation such as NIST CSF (Cyber Security Framework) or OWASP (Open Web Application Security Project).
The first stage of RECONNAISSANCE begins with the formal approval of scope of work, this is where you’re looking at the company’s website to find out what they have and what they don’t have in terms of security controls. During INTRUDE stage an attack is simulated in a controlled environment to exploit vulnerabilities and risks.
During the SORT stage all fact findings from the previous stages are sorted, quantified, and flag as low-medium-high. ESCORT stage prompts management for an immediate response, rectification, and escort operations against business risks.
Comprehensive REPORT is generated with the best possible recommendations and guidelines for our clients to fix issues themselves or hire our 24×7 online assistance and monitoring services.
People also explored (blogs):
- https://shieldonsystems.com/2022/11/21/cyber-security/
- https://shieldonsystems.com/2022/12/07/cyber-security-top-emerging-attacks-in-2023/
- https://shieldonsystems.com/2022/12/13/everthing-you-need-to-know-about-hackers-and-hacking/
- https://shieldonsystems.com/2022/12/13/what-to-do-if-you-are-a-victim-of-a-cyber-attack-or-cyber-crime/
- https://www.shieldonsystems.com/2023/01/01/cyber-security-attacks-in-pakistan-2022/
Author: C. IMRAN
IT Program Manager, Business Owner (www.shieldonsystems.com)
We work with a variety of technologies, platforms, and frameworks to help you develop custom eCommerce & software solutions, build mobile applications, & provide cybersecurity services. We also provide training and support to ensure the successful implementation and maintenance of the solutions. With our expertise, you can be confident that your business will be able to stay ahead of the competition and achieve success.
LinkedIn: https://www.linkedin.com/company/shield-on-systems
Facebook: https://www.facebook.com/SOSWEBAUDITFIX
Instagram: https://www.instagram.com/shieldonsystems
Twitter: https://twitter.com/fix_sos
Email: [email protected]
